Talare i världsklass
Branschledande experter delar erfarenheter & framtidsspaningar.
Välkommen till Identity Day, där vi för fjärde året i rad samlar några av branschens främsta experterna inom Identitetssäkerhet för att dela insikter, verktyg och strategier för att skydda din organisation mot cyberhot och dataintrång.
Under eventet får du ta del av inspirerande föreläsningar om de senaste trenderna och kommande utmaningar, och lära dig vilka lösningar som är mest effektiva för att stärka din organisations säkerhet.
Dyk djupare i våra breakout-sessioner och få expertkunskap inom viktiga områden som IAM, IGA, PAM, AM och mycket mer.
Ett perfekt tillfälle att nätverka med branschkollegor och njuta av god mat och dryck helt kostnadsfritt. Eventet hålls på svenska, med vissa presentationer på engelska.
Boka din plats och var med på årets mest inspirerande event!


Branschledande experter delar erfarenheter & framtidsspaningar.
Lär dig nya saker och få verktyg att ta med tillbaka till dina kollegor.
Knyt nya kontakter med andra i branschen och bygg ditt nätverk.
Vi ses i trevliga och inspirerande lokaler på Posthuset 7A i Stockholm.
Förutom inspiration så bjuder dagen på ett par överraskningar.
Välsmakande mat och dryck serveras under hela dagen och kvällen.

Keynote
Ta del av ett spännande scensamtal där Sara Wimmercranz möter vår moderator Johanna Samuelsson för en inspirerande diskussion om trender och insikter som formar framtidens näringsliv och samhälle.
Hon var med och grundade Footway och riskkapitalbolaget BackingMinds, som gör affärer på andra investerares fördomar. Sara ägnar sitt liv åt att demokratisera ägandet och att bygga broar mellan vanligt folk och näringslivet och vurmar för varje människas makt att göra skillnad. Ju fler entreprenörer som får tillgång till kapital, desto fler problem kommer att lösas. Sara har blivit utsedd till en av Sveriges mäktigaste tech-investerare av Dagens Industri och Årets Mama av tidningen Mama. Senast utsågs hon till ”Sveriges Viktigaste Kvinnliga Investerare” av Dagens Industri, som erkänner hennes roll i att omforma riskkapitalbranschen och hon rankades också som Sveriges mäktigaste inom ekonomi på instagram av Medieakademins Maktbarometer.

“What is Identity Fabric? Why Identity Fabric? How to approach it”
You are very likely to have heard of an Identity Fabric, but many of us have not had the necessary time or opportunity to delve into it. In this session we will consider what it is, why there is a focus on it and what we as individual Identity Security professionals should be thinking about in our approach to it.
Rudy de Sousa has over 15 years consulting, solution design and technical experience in Identity. He works with some of the largest organisations world-wide, with particular focus in Europe, Middle East and Africa, to help organisations achieve successful and efficient Identity outcomes. Rudy is EMEA Presales Director for One Identity, covering Privileged Access Management, Access Management, Identity Governance and Administration, and Active Directory Management.

"Securing APIs with Identity: Tackling Token Abuse and Preventing Data Leaks"
API breaches continue to rise, driving some of the most significant data exposures in recent years. In this talk, Daniel Lindau explores how flawed access patterns and mismanaged tokens leave APIs and identity data vulnerable to misuse.
You’ll gain insights into why traditional OAuth patterns often fall short in today’s complex API environments. By adopting modern techniques like the token handler and FAPI standards, you can tighten access control and build resilience into your API architecture.
At the core of this challenge is Customer Identity and Access Management (CIAM). As organizations expose APIs to customers, partners, and developers, CIAM is key to enforcing identity-aware access policies, managing user consent, and protecting sensitive data. Robust CIAM is essential for both API security and delivering secure, compliant digital experiences at scale.
Daniel will also cover B2B and partner use cases, where external integrations add complexity. Expect practical, identity-driven strategies to secure public APIs, internal systems, and third-party interfaces.
Daniel Lindau is an identity specialist and Technical Director of Professional Services at Curity. He spends his days helping companies of all sizes design standards-based solutions to manage identities, secure APIs, and comply with regulations. He has a background as an application developer and broad experience in building solutions with standards such as SAML, SCIM, OAuth2, OpenID Connect, and FAPI.

"Designing Trust for the Future of B2B Digital Identity"
The B2B landscape is evolving beyond transactions. In the era of B2B(2X), organisations must securely interact with partners, suppliers, employees, and customers. Trust is now a strategic imperative. To unlock opportunities, businesses need intelligent identity solutions. AI-driven risk analysis, decentralized identity, and advanced verification frameworks help mitigate risks, prevent fraud, and ensure seamless access. Join this session to learn how companies are reducing onboarding times, strengthening security, and streamlining digital interactions with scalable identity frameworks.
As a Senior Director of Product Management, Matt is responsible for building product strategies in bringing the PingIdentity product portfolio to market. Matt works closely with customers and partners to understand their current and strategic business needs in order to convert them identity outcomes that the product teams can deliver, resulting in the most modern and comprehensive platform in IAM. Prior to joining PingIdentity, Matt has over 25 years experience in the Identity Management and Security space working with companies such as Oracle, Symantec, Unisys, ForgeRock, and Passlogix.

"The cornerstone for revolutionized identity security"
Modernization isn’t just an option in today’s fast-moving digital world – it’s essential for organizations that want to stay secure and competitive. Transform your identity security approach. Ensure audit readiness and governance across your environment with enhanced data hygiene. Proactively detect identity and access risks before they become incidents while minimizing manual efforts and prioritizing risk remediation. Cut costs, save time, and stay compliant, all with one powerful platform.
Paul is lead partner enablement in EMEA at Saviynt for and brings more than 20 years’ experience in identity management.

Moderator
Dagen leds av Johanna Samuelson – en erfaren och engagerande konferencier som med skärpa, värme och humor guidar dig genom programmet.
Johanna Samuelson är en erfaren och uppskattad konferencier, programledare och komiker, känd för sin kvicktänkthet, humor och värme. Med en bakgrund inom teater och stand-up har hon en unik förmåga att fånga publiken och skapa en levande atmosfär på scen.
Johanna har tidigare lett evenemang för stora koncerner som DHL, Cygate och LeoVegas, och har även arbetat internationellt. Detta blir hennes fjärde år som konferencier på Identity Day-scenen.

"Winning the Privileged Access Battle: From Firefighting to Field Control"
Organisations today face a critical privileged access problem that puts them in constant firefighting mode. Despite deploying the ”right” tools such as PAM or IGA, privilege controls continue to fail, leaving security teams reactive rather than strategic.
Drawing from real-world experience scaling IAM at a large multi-national retailers and insights from red team exercises, this session reveals why traditional approaches fall short and presents a practical framework for building resilient privileged access controls, designed for today’s threat environment.
Key Takeaways:
This session provides actionable strategies for security and identity professionals looking to move beyond firefighting toward proactive, confident privileged access protection.
Rob Ainscough is the Chief Identity Security Advisor at Silverfort and a seasoned leader in identity and access management. With over a decade of experience building and scaling IAM programs in complex, global environments, Rob brings deep expertise in access governance, privileged access, and secure credentialing. He is known for simplifying identity security challenges and driving automation and risk reduction at scale.

“Breaking Free: Embracing Truly Agnostic IAM for a Modern Identity Landscape”
Digital identities have been part of our lives long enough to leave behind a patchwork of databases, rigid processes, vendor lock-ins, and outdated architectures. This session challenges the notion that a ”one-vendor IAM stack” is the only path forward. Anders Björk will explore the power of a truly agnostic approach to Identity and Access Management—one that puts flexibility, scalability, and user experience first. From internal workforce identities to CIAM, external access, and JML (Joiner-Mover-Leaver) flows, discover how decoupling your IAM strategy can future-proof your architecture and empower your organization to adapt faster, integrate smarter, and innovate freely.
With a strong technical foundation and deep expertise in digital identity and access management (IAM), Anders brings a unique blend of engineering acumen and strategic vision to the stage. As a seasoned professional in the IAM space, Anders plays a pivotal role in sales engineering, solution architecture, and defining product requirements—bridging the gap between complex technology and real-world business needs. A passionate IAM evangelist and prolific blog writer, Anders is dedicated to making digital identity accessible and actionable. Beyond thought leadership, they also create compelling marketing assets including instructional videos, use case guides, solution documents, and step-by-step technical tutorials. Whether driving product innovation or educating the industry, Anders is known for delivering insights with clarity, energy, and impact.

”A realistic and pragmatic approach to AI”
By using existing AI and Machine Learning functionality in combination with integrated IGA and PAM, organizations can achieve significant security benefits. As a result, higher security can be achieved and where affected actors, such as managers, system administrators and IT auditors, are effectively supported in their work.
Ingvar Johansson is an IT professional with more than 35 years in the IT industry. Ingvar has been focusing on Identity and Access Governance for the last 20+ years working for several leading IGA vendors. Ingvar is currently working at One Identity as a Principal Solutions Architect focusing on IAM in the EMEA region. Ingvar’s primary responsibility has always been as a solutions architect in a pre-sale role with the additional responsibility as a technical architect/consultant.

“Have we lost our Identity in a world of compliance?”
Identity is more critical than ever, it´s the foundation of who we are, guiding our values, decisions, and interactions with the world. Within the context of compliance and digital security, identity becomes even more significant. In a world where personal data is constantly at risk of being hacked or manipulated, maintaining a clear and secure sense of identity is essential to protect not just our personal information, but our autonomy and control.
With over 20 years of experience in Identity and Access Management (IAM), Sören specialize in Identity Lifecycle Management, Identity Governance, and Zero Trust Architectures.

"AI at your Service"
Imagine a future where AI seamlessly handles Identity Governance and Administration (IGA) tasks—whether you’re an administrator, a helpdesk agent, or an end user. Instead of navigating complex workflows and esoteric User Interfaces, AI will be at your service, executing tasks through natural language interactions. Join us as we walk through a dream scenario of reliable AI integration, showcasing how conversational AI can revolutionize identity management, streamline operations, and enhance security—all while reducing manual effort and human error.
With over 25 years of global experience in cybersecurity and a focus on Identity & Access Management, Paul Walker is a seasoned professional known for his exceptional communication and problem-solving skills. Currently serving as a Field Strategist at Omada, he brings a wealth of expertise in value selling, product growth, and IAM solution evangelism. Paul has held key positions at Clear Skye, One Identity, and Dell, consistently driving technical strategy and maintaining impactful relationships with customers and partners throughout his distinguished career.

"Enabling Continuous Trust Through Verifiable Credentials, Low-Friction Authentication, and Identity Verification"
Traditional perimeter-based identity models are no longer sufficient in an environment where threats are persistent, identities are dynamic, and user interactions span multiple devices and platforms. This technical workshop will dive deep into how continuous trust models can be architected using decentralized identity technologies, low-friction authentication mechanisms, and real-time verification processes.
Samudra Gupta works as a Senior Sales Engineer at Ping Identity.

"Beyond Privileged Accounts: Modern PAM for Today’s Dynamic, Hybrid World"
Even with growing budgets and stricter compliance mandates, cyber risk is still on the rise. Identities are a top target, with attackers exploiting hidden Paths to Privilege™ to gain access. Managing elevated permissions across hybrid environments is complex, and traditional PAM tools—focused only on privileged accounts—often leave gaps. This session will look at how modern, identity-focused PAM secures all users, reduces risk, and simplifies access to keep your organization both protected and productive.
Matthew Sturman works as a Lead Solution Engineer at BeyondTrust where he is committed to understanding the threats faced by organisations and helping find solutions to fulfil their security requirements. Matt has helped many organisations balance security and user productivity across their estate by enabling frictionless privilege management solutions. With a range of experience across software houses and large system integrators, Matt specialises in Endpoint Privilege Management.

"Tomorrow will be different"
The future is spelled A.I., and it’s rewriting Identity Security in more ways than we dare to admit.
Get ready for a thought-provoking journey from the messy present to the autonomous future of Identity. This talk explores the explosive evolution of both AI and Identity Security, challenging us to look beyond today’s manual toil and into a redefined world powered by AI Native technology.
Sami Mäkelä, CTO at ID North, brings nearly 30 years of experience in system development, IT risk, and security. His expertise spans Identity and Access Management (IAM), Security Information and Event Management (SIEM), Identity & Access Governance, as well as risk and quality metrics. Throughout his career, Sami has combined deep technical knowledge with strategic insight to deliver secure, scalable, and future-ready solutions.

"Why the Identity Graph is key to the future of Identity Security"
Mikael Wikström works as a Cyber Security Technical Advisor covering the Nordics region where he assists enterprises and organizations in defining the strategy and adoption of an integrated Identity Governance Platform. Mikael has more than 30 years experience in the Cyber Security software industry, where he has lead teams in the development and implementation of complex Cyber Security solutions with a focus on Identity Governance, Identity Management, Access Management in a wide range of organizations and enterprises.

"Weaving the Future"
Identity is no longer an IT side note it’s the foundation of digital trust and business growth.
This session uncovers how Identity Fabric turns today’s fragmented systems into one unified strategy, driving ROI, agility, and resilience in the AI era. The organizations that master it will lead. The rest will be left unraveling the loose threads.
With over 25 years in B2B sales, Anders Rönnquist specializes in innovative IT solutions, particularly in identity and access management (IAM) and security. His strategic approach enhances business efficiency and drives digital transformation. As a trusted advisor and strategic partner, Anders and his team ensure secure access and protection of sensitive information. He leads the sales team to drive revenue growth, expand market share, and align business development initiatives with organizational goals.

"Weaving the Future"
Identity is no longer an IT side note it’s the foundation of digital trust and business growth.
This session uncovers how Identity Fabric turns today’s fragmented systems into one unified strategy, driving ROI, agility, and resilience in the AI era. The organizations that master it will lead. The rest will be left unraveling the loose threads.
With over 25 years of experience in IT and cybersecurity, Anders is a visionary leader specializing in Identity Security. His strategic and technical expertise drives innovation and ensures clients’ digital identities are protected against evolving threats. Anders is recognized for his forward-thinking approach, keeping Arctic Group at the forefront of the industry.

"Compliance at the Speed of Business"
Managing compliance manually can be time-consuming and prone to errors. Removing the errors of manual evidence collecting to using a solution that automates the compliance process, enabling organisations to maintain continuous adherence to frameworks like NIS 2, DORA, SOC 2, ISO, and beyond.
Joe has been with Drata for three months as a Solutions Engineer, supporting organizations in achieving security and compliance through automation. Prior to joining Drata, he spent four years at Okta in the Identity and Access Management space, working across the channel in EMEA and the Middle East. Before moving into pre-sales, Joe began his technical career as a software engineer working for a fintech company, before moving into presales

"The Secure Employee Journey – Powered by Microsoft Entra Suite"
An employee’s digital identity has a lifecycle that starts even before their first day and continues until after they leave the organization. In this session, we will follow that journey step by step:
Before day one – the individual’s identity is securely verified, establishing trust from the very beginning.
First day and beyond – the right access is automatically granted based on role and responsibility. Additional access can be requested through self-service with optional approval, while regular access reviews ensure that permissions remain appropriate over time.
Adaptive protection – risks and threats are continuously assessed, keeping logins and access secure, with self-remediation options for users.
Secure connectivity anywhere – whether resources are in the cloud, on-premises, or across the internet, employees gain consistent, secure access from any device and location, ensuring productivity without compromising security.
End of the journey – when employment ends, access is swiftly and cleanly removed, minimizing risks to the organization.
This session demonstrates how modern identity solutions based on Microsoft Entra Suite can deliver both stronger protection and a smoother user experience throughout the entire employee journey.
Tom Aafloen is a technology professional based in Karlstad with a strong focus on identity and access management. With extensive experience in Microsoft solutions, Tom is passionate about helping organizations modernize their identity infrastructure. His recent work has centered on the Entra ID Suite, exploring how smarter identity can enhance security and user experience. He enjoys sharing insights that empower teams to make informed decisions about digital identity.

"Driving Identity Security with JIT Access and Zero Standing Privilege for Intelligent Next-Generation Access Modeling"
As hybrid environments grow more complex and remote work becomes the norm, identity has emerged as the new security perimeter. This session explores the tools and strategies needed to build and maintain a modern, identity-centric security model aligned with Zero Trust principles.We’ll cover practical insights and real-world examples that show how leading organizations achieve continuous trust and compliance by:
– Eliminating Standing Privilege: Implementing Zero Standing Privilege (ZSP) to minimize the attack surface across systems and applications.
– Driving Intelligent Access: Leveraging Identity Governance and Privileged Access Management (PAM) to automate access reviews and enable Just-in-Time (JIT) elevation based on context and risk.
– Scaling Security with AI: Using machine learning to streamline compliance, detect anomalous behavior, and simplify audits in complex environments.
Discover how to integrate governance and privilege capabilities to gain end-to-end visibility, reduce manual overhead, and significantly lower enterprise risk.
Søren Källstrøm is a Senior Solutions Engineer at Saviynt, focused on architecting the next generation of identity-centric security. With deep expertise in Access Management and Identity Governance, he specializes in applying Identity-First and Zero Trust principles across complex hybrid and multi-cloud environments. Passionate about placing identity at the center of cybersecurity, Søren works with organizations to design practical, scalable solutions that enhance resilience and reduce risk.

Starta dagen med en god frukost och värdefullt nätverkande.

Vår briljanta moderator Johanna inleder dagen tillsammans med Fredrik Åström, CEO på Arctic Group, och Jens Björkman, CEO på ID North.

You are very likely to have heard of an Identity Fabric, but many of us have not had the necessary time or opportunity to delve into it. In this session we will consider what it is, why there is a focus on it and what we as individual Identity Security professionals should be thinking about in our approach to it.

Modernization isn’t just an option in today’s fast-moving digital world – it’s essential for organizations that want to stay secure and competitive. Transform your identity security approach. Ensure audit readiness and governance across your environment with enhanced data hygiene. Proactively detect identity and access risks before they become incidents while minimizing manual efforts and prioritizing risk remediation. Cut costs, save time, and stay compliant, all with one powerful platform.

The B2B landscape is evolving beyond transactions. In the era of B2B(2X), organisations must securely interact with partners, suppliers, employees, and customers. Trust is now a strategic imperative. To unlock opportunities, businesses need intelligent identity solutions. AI-driven risk analysis, decentralized identity, and advanced verification frameworks help mitigate risks, prevent fraud, and ensure seamless access. Join this session to learn how companies are reducing onboarding times, strengthening security, and streamlining digital interactions with scalable identity frameworks.

Identity is no longer an IT side note it’s the foundation of digital trust and business growth. This session uncovers how Identity Fabric turns today’s fragmented systems into one unified strategy, driving ROI, agility, and resilience in the AI era. The organizations that master it will lead. The rest will be left unraveling the loose threads.

Njut av en välsmakande fika, sponsrad av våra härliga sponsorer: OpenText, Curity, BeyondTrust och Fortified ID.

Identity is more critical than ever, it´s the foundation of who we are, guiding our values, decisions, and interactions with the world. Within the context of compliance and digital security, identity becomes even more significant. In a world where personal data is constantly at risk of being hacked or manipulated, maintaining a clear and secure sense of identity is essential to protect not just our personal information, but our autonomy and control.

API breaches continue to rise, driving some of the most significant data exposures in recent years. In this talk, Daniel Lindau explores how flawed access patterns and mismanaged tokens leave APIs and identity data vulnerable to misuse. You’ll gain insights into why traditional OAuth patterns often fall short in today’s complex API environments. By adopting modern techniques like the token handler and FAPI standards, you can tighten access control and build resilience into your API architecture.

Even with growing budgets and stricter compliance mandates, cyber risk is still on the rise. Identities are a top target, with attackers exploiting hidden Paths to Privilege™ to gain access. Managing elevated permissions across hybrid environments is complex, and traditional PAM tools—focused only on privileged accounts—often leave gaps. This session will look at how modern, identity-focused PAM secures all users, reduces risk, and simplifies access to keep your organization both protected and productive.


Digital identities have been part of our lives long enough to leave behind a patchwork of databases, rigid processes, vendor lock-ins, and outdated architectures. This session challenges the notion that a ”one-vendor IAM stack” is the only path forward. Anders Björk will explore the power of a truly agnostic approach to Identity and Access Management—one that puts flexibility, scalability, and user experience first. From internal workforce identities to CIAM, external access, and JML (Joiner-Mover-Leaver) flows, discover how decoupling your IAM strategy can future-proof your architecture and empower your organization to adapt faster, integrate smarter, and innovate freely.

Managing compliance manually can be time-consuming and prone to errors. Removing the errors of manual evidence collecting to using a solution that automates the compliance process, enabling organisations to maintain continuous adherence to frameworks like NIS 2, DORA, SOC 2, ISO, and beyond.

An employee’s digital identity has a lifecycle that starts even before their first day and continues until after they leave the organization. In this session, we will follow that journey step by step. This session demonstrates how modern identity solutions based on Microsoft Entra Suite can deliver both stronger protection and a smoother user experience throughout the entire employee journey.

Vi bjuder på en välsmakande lunch, sponsrad av Omada, Silverfort och SailPoint. Passa på att nätverka med branschkollegor och hälsa på våra sponsorer i deras montrar.

By using existing AI and Machine Learning functionality in combination with integrated IGA and PAM, organizations can achieve significant security benefits. As a result, higher security can be achieved and where affected actors, such as managers, system administrators and IT auditors, are effectively supported in their work.

Traditional perimeter-based identity models are no longer sufficient in an environment where threats are persistent, identities are dynamic, and user interactions span multiple devices and platforms. This technical workshop will dive deep into how continuous trust models can be architected using decentralized identity technologies, low-friction authentication mechanisms, and real-time verification processes.

As hybrid environments grow more complex and remote work becomes the norm, identity has emerged as the new security perimeter. This session explores the tools and strategies needed to build and maintain a modern, identity-centric security model aligned with Zero Trust principles.We’ll cover practical insights and real-world examples that show how leading organizations achieve continuous trust and compliance.

Dagens breakout sessions är nu avslutade och programmet fortsätter på stora scenen.

Imagine a future where AI seamlessly handles Identity Governance and Administration (IGA) tasks—whether you’re an administrator, a helpdesk agent, or an end user. Instead of navigating complex workflows and esoteric User Interfaces, AI will be at your service, executing tasks through natural language interactions. Join us as we walk through a dream scenario of reliable AI integration, showcasing how conversational AI can revolutionize identity management, streamline operations, and enhance security—all while reducing manual effort and human error.

Organisations today face a critical privileged access problem that puts them in constant firefighting mode. Despite deploying the ”right” tools such as PAM or IGA, privilege controls continue to fail, leaving security teams reactive rather than strategic. Drawing from real-world experience scaling IAM at a large multi-national retailers and insights from red team exercises, this session reveals why traditional approaches fall short and presents a practical framework for building resilient privileged access controls, designed for today’s threat environment.

Njut av en välsmakande fika, sponsrad av våra härliga sponsorer: OpenText, Curity, BeyondTrust och Fortified ID.

- Learn why governance and security always starts with insight.
- Discover how a modern data model strengthens identity security.
- Hear how a platform approach simplifies and enhances identity management.
- Learn from the leader in Identity Security why this is just the beginning – and find out what’s next for identity security.

The future is spelled A.I., and it’s rewriting Identity Security in more ways than we dare to admit. Get ready for a thought-provoking journey from the messy present to the autonomous future of Identity. This talk explores the explosive evolution of both AI and Identity Security, challenging us to look beyond today's manual toil and into a redefined world powered by AI Native technology.

Ta en välbehövlig bensträckare, fyll på kaffekoppen och passa på att mingla med våra sponsorer under pausen.

Paneldiskussion med våra experter från One Identity, Ping Identity, Saviynt, Omada, SailPoint & Silverfort.

Finalen bjuder på ett samtal med Sara Wimmercranz – en av Sveriges starkaste röster inom tech. Hör hennes tankar om cybersäkerhet som konkurrenskraft, synen på AI, och de möjligheter och utmaningar företag möter med nya lagstiftningar. Tillsammans med vår moderator Johanna Samuelsson blickar hon också framåt mot vad som väntar runt hörnet. 👉 Ett samtal du absolut inte vill missa!

Följ med oss in i kvällen – börja med ett glas bubbel, njut av en härlig middag och låt dig överraskas av ett magiskt inslag. 🪄 Kvällen sponsras av One Identity, Ping Identity och Saviynt.
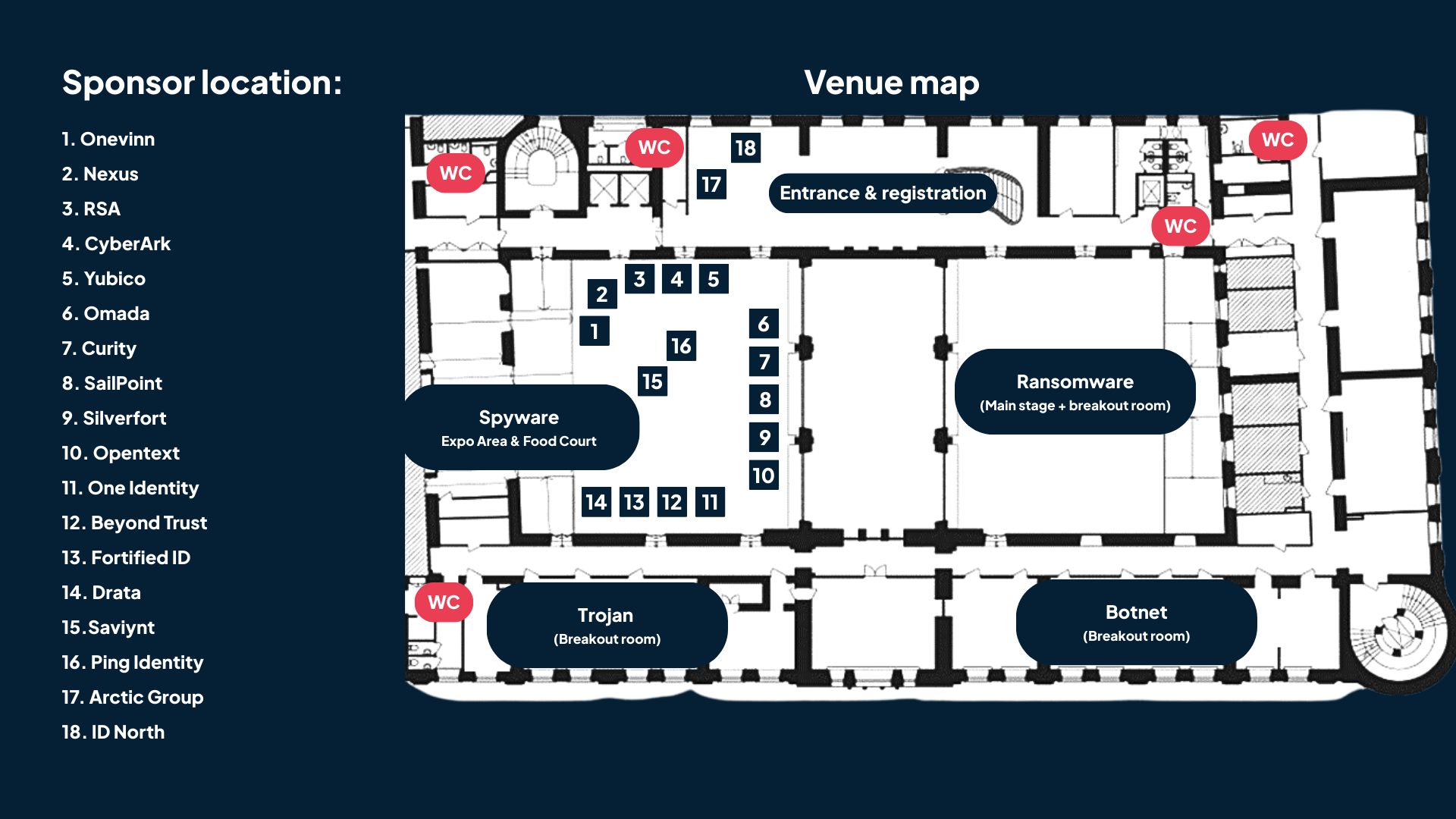































Arctic Group är din strategiska partner för att ta nästa steg mot ökad säkerhet. Vi hjälper er att stärka er digitala infrastruktur och skydda er verksamhet mot framtidens utmaningar. Med vår expertis inom cybersäkerhet och digitalisering ser vi till att ni kan möta nya utmaningar med trygghet och innovation. Tillsammans bygger vi en hållbar och säker digital framtid för er.

Vi på ID North är specialiserade inom identitetssäkerhet och hjälper ditt företag att skydda och hantera era digitala identiteter. Med oss får du tillgång till branschens främsta experter och den senaste tekniken. Våra lösningar säkerställer effektivitet, smidiga processer, omfattande kontroll och skydd på högsta nivå. Tillsammans skapar vi en stabil grund för tillit, innovation och framgång. Säkra din organisations framtid med oss.
Ja! Även om eventet är kostnadsfritt, vill vi gärna påminna om att det krävs en föranmälan för att delta. Vi ser verkligen fram emot att välkomna er och vill säkerställa att alla får en fantastisk upplevelse!
Nej! Då det är ett kostnadsfritt event har vi begränsat antal platser. Vi kommer inte kunna ta emot anmälningar på plats vid eventet, så säkra din plats redan idag!
Eventet är till för alla företag / organisationer som verkar i digitala miljöer. Arbetar ni med hybrida arbetsplatser? Har du en digital profil? Hanterar ni personliga uppgifter? Då är identitetssäkerhet av högsta relevans.
Självklart, se bara till att anmäla er så rätt mängd mat och platser finns. Bjud med en vän eller en kollega och anmäl er idag.
Nätverk, mat & mingel. På plats under dagen och kvällen kommer du även ha möjlighet att knyta kontakter inom branschen, underhållas och äta gott.
Eventet är på svenska med inslag av presentationer som hålls på engelska.